
Hello hackers! Today, I am going to talk about Google Hacking also known as Google Dorking. In this guide, we’ll explore how hackers use Google to find unsecured files, vulnerable CCTVs, database passwords, and how you can protect your CCTVs and websites from cyber criminals.
Table of Contents
What is Google Dorking?
Let’s start with the basics. Google Dorking, also known as Google hacking, is a sophisticated method of refining search queries to uncover specific information that may not be readily accessible through conventional search methods. It’s like having a secret key to unlock hidden doors on the internet.
Imagine you’re searching for something specific, like a rare book or a technical manual. Instead of sifting through countless search results, Google Dorking allows you to use special search operators and symbols to narrow down your search and find exactly what you’re looking for.
I have also uploaded a video on How to use Google Dorks. Here’s the video:
Logical Operators and Symbols in Google Search
Now, let’s delve into the magic behind Google Dorking – the logical operators and symbols that make it all possible. These are like secret codes that tell Google how to interpret your search query:
- site: Limits your search to a specific website or domain. For example, “
site:wikipedia.org” will only show results from Wikipedia. - filetype: Helps you find specific types of files, such as PDFs, DOCs, or XLS. You can use it like “
filetype:pdf” to search for PDF documents. - intitle: Searches for specific words in the title of web pages. This is handy when you’re looking for pages with a particular title.
- inurl: Looks for keywords within the URL of web pages. It’s useful for finding pages with specific words in their URLs.
By combining these operators creatively, you can craft powerful search queries that yield highly relevant results, saving you time and effort in your online searches.
Simple Search Operator to Find a Filetype
Let’s say you’re a student working on a research project and need to find scholarly articles in PDF format. Instead of scrolling through endless search results, you can use the "filetype:pdf" operator along with relevant keywords to narrow down your search and find scholarly PDFs quickly and efficiently.
For instance, try searching for "site:edu filetype:pdf cybersecurity" to find educational resources on cybersecurity in PDF format from university websites.
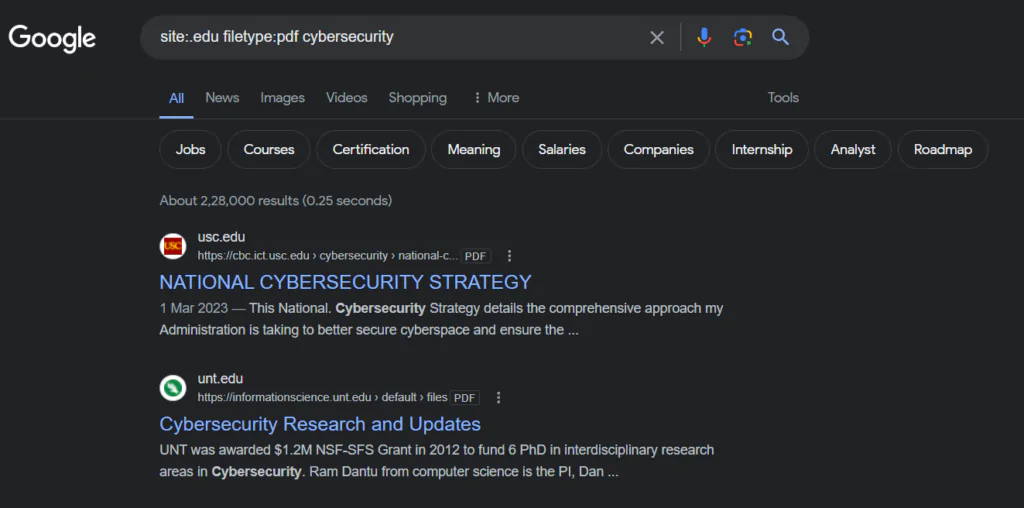
How Hackers Use Google to Find Vulnerable Webcams?
Now, let’s shift our focus to a darker side of Google Dorking – how hackers can exploit this technique to find vulnerable webcams and gain unauthorized access to them.
Imagine you’re innocently browsing the internet when suddenly, your webcam turns on without your consent. How is this possible? Well, hackers often use advanced search queries like "intitle:'webcamXP 5' inurl:8080" to identify webcams that are not properly secured.
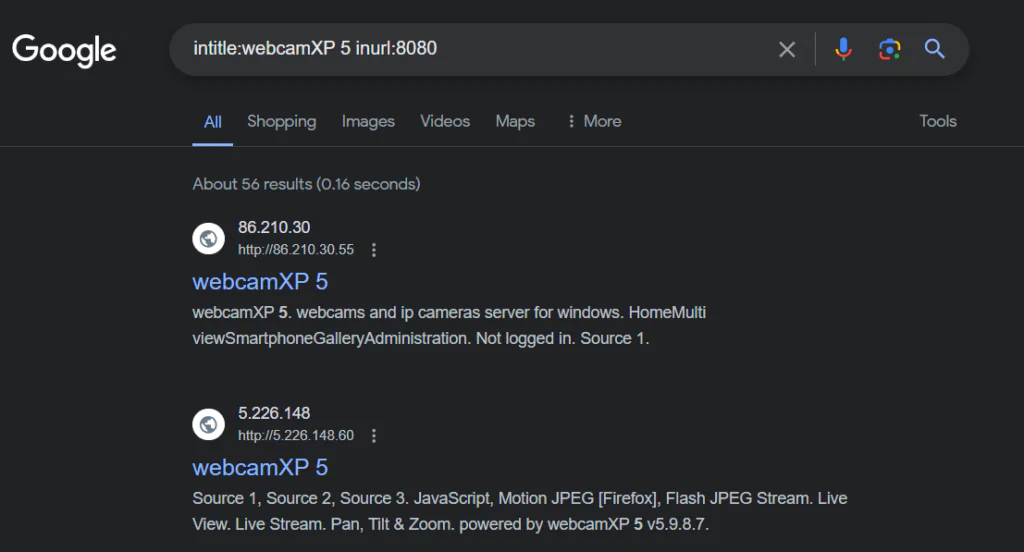
The "intitle" operator looks for specific words in the title of web pages, while "inurl" searches for keywords within URLs. In this case, the query targets webcams using the "webcamXP 5" software and accessible via port 8080. By exploiting security loopholes in these webcams, hackers can potentially spy on unsuspecting individuals or even compromise sensitive information.
You can also find out vulnerable webcams or CCTV cameras using Shodan. I’ve got a detailed article all about it. Just click here: [HOW WEBCAMS CAN BE VULNERABLE TO HACKING THROUGH SHODAN]. It explains how Shodan can help spot security problems in webcams and CCTVs.
How Hackers Use google to find Database PasswordS?
Another concerning aspect of Google Dorking is its potential to uncover sensitive information such as database passwords. Hackers can use search queries like "db_password filetype:env" to search for environment files containing database credentials.
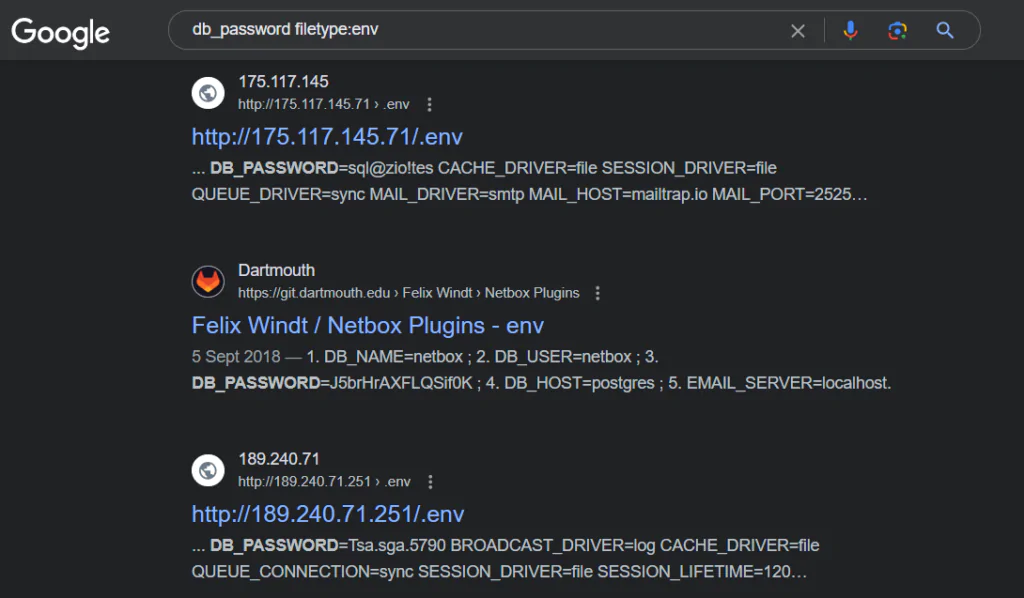
These environment files, often used in web development environments, may contain sensitive information like database usernames, passwords, and server configurations. If these files are exposed to the public through misconfigurations or security oversights, hackers can exploit them to gain unauthorized access to databases and potentially wreak havoc on websites or systems.
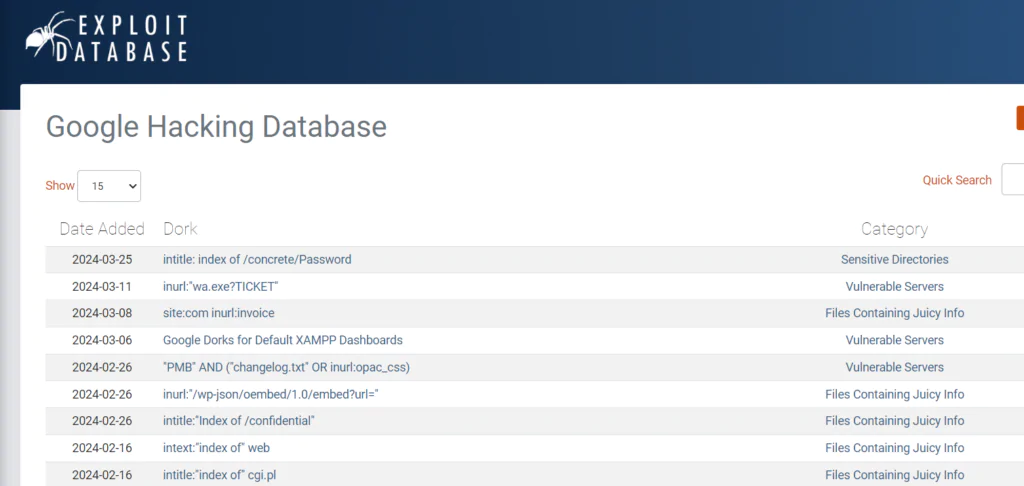
How to Use Exploit DB Database for This
Exploit DB is a treasure of known vulnerabilities and exploits that hackers can leverage to their advantage. By combining Google Dorking with data from Exploit DB, hackers can target specific vulnerabilities in websites, applications, or systems and launch targeted attacks.
For example, a hacker might use Google Dorking to identify websites running outdated software versions known to have security vulnerabilities. They can then cross-reference these vulnerabilities with entries in Exploit DB to find ready-made exploits or attack vectors, making their malicious activities more efficient and potent.
How to Prevent Your Webcams and Websites
Now that we’ve explored the potential risks associated with Google Dorking, let’s shift our focus to proactive measures you can take to protect yourself, your webcams, and your websites from potential threats:
- Secure Your Webcams: Ensure that your webcams have strong passwords and are not accessible through public URLs. Disable remote access features unless absolutely necessary, and regularly update firmware to patch known vulnerabilities.
- Strengthen Website Security: Implement robust security measures on your websites, including firewalls, HTTPS encryption, secure authentication methods, and regular security audits. Keep software and plugins updated to mitigate known vulnerabilities.
- Educate Yourself and Others: Stay informed about emerging cybersecurity threats and best practices. Educate yourself and others about the importance of online security, privacy settings, and safe browsing habits to minimize risks.
- Monitor and Respond: Regularly monitor your webcams, websites, and server logs for suspicious activities. Have incident response plans in place to quickly address and mitigate security incidents if they occur.
Conclusion
In conclusion, Google Dorking is a powerful search technique that can be used for both legitimate purposes and malicious activities. By understanding how it works and implementing proactive security measures, you can enhance your online search experience while safeguarding your privacy and security.
Remember, with great power comes great responsibility. Use Google Dorking responsibly, stay informed about cybersecurity threats, and take proactive steps to protect yourself and your digital assets from potential risks.
Dell Data Breach Exposes 49 Million Customer Records
The recent news of a Dell data breach has raised eyebrows across the tech world,…
Advanced Phishing Using NoVNC: Breaking Through 2FA
Hello and welcome! Today, we’re diving into the world of NoVNC-based advanced phishing attacks. Ever…
Hacked!: British Columbia Government Faces Major Hacking Attempt
HIGHLIGHTS: British Columbia’s government confirms sophisticated cyberattack on its information systems Premier David Eby and…
NETCAT 101: What is Netcat and Its Practical Uses in Networking
Bluetooth Hacking Made Simple: 5 Tools Uncovered
Welcome to the world of Bluetooth hacking! In this section, we’ll explore the basics of…
3 Powerful Techniques for Creating a Backdoor Practically and Maintaining Persistent Access
Introduction In this comprehensive tutorial, we will delve deeply into the techniques employed by hackers…











I’ve been visiting this site for years, and it never fails to impress me with its fresh perspectives and wealth of knowledge. The attention to detail and commitment to quality is evident. This is a true asset for anyone seeking to learn and grow.
Pingback: https://hackproofhacks.com/google-dorking-how-t...